Hi Guys,
I have been working with Microsoft Azure AD Application Proxy connector lately to publish Applications in the Azure and I came across an issue that although the Microsoft Azure AD Application Proxy connector was installed and running on the on-premise server, it was not fully functional with the Microsoft Azure AD Application Proxy portal.
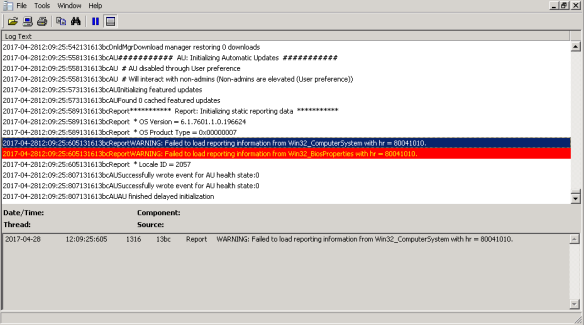
Error location: Event Viewer> Applications and services logs>Microsoft>AadApplicationProxy>Updater
Error log: The Connector Update Service failed to check for an update.
If this error persists, please use the following link to verify that all necessary ports are open in your firewall: https://go.microsoft.com/fwlink/?linkid=843463.
For more details, please see our troubleshooting page: http://go.microsoft.com/fwlink/?LinkID=512316&clcid=0x409.
Additional details: ‘Unable to connect to the remote server’.
Root cause: once you install the Microsoft Azure AD Application Proxy connector, its adds 2 Services to your host server the Microsoft AAD Application Proxy Connector and the Microsoft AAD Application Proxy Connector Updater.
However it appears that the Microsoft AAD Application Proxy Connector Updater service requires access to the Service Bus control channels that the connector service uses also require connectivity to specific IP addresses. This is the official line from Microsoft until Service Bus moves to an FQDN instead. My client was not happy but here are the options to resolve the issue.
Solution: There are two solutions
- Configure connectors config to bypass your on-premises outbound proxies.
- Configure connectors config to use an outbound proxy to access Azure AD Application Proxy.
This is the official Microsoft Link for Configuring both options: Application-proxy-working-with-proxy-servers
However what I found was that you are better off using a bit of both during the installation of the Azure AD Application Proxy connector because most proxy solution like Bluecoat, you can whitelist the URLs but not the IP range.
Actually more Urls popped up than Microsoft has listed because the Urls keep bouncing from one domain to another which is secure but hard to manage.
- //management.azure.com/
- //*.azure.com/
- //*.microsoftonline.com/
- //login.microsoftonline.com/
- //login.windows.net/
- //*.microsoft.com/
- //portal.azure.com/
- //www.microsoft.com/
- //microsoft.com/
- //symcb.com/
- //ocsp.verisign.com/
- //crl.verisign.com/
- //symcd.com/
- //*.msappproxy.net/
- //*.servicebus.windows.net
Once you verify that the Connector services has installed successfully and Running.
Check that both Service have installed
Then you need to Allow the connector outbound access to Azure datacenter IP ranges. from your Azure Application Proxy connector server only for Security reason obviously.
Only then will the Azure AD Application Proxy Connector work with the Azure AD Application Proxy service.